# H3C防火墙-对象策略访问配置
# 实验拓扑
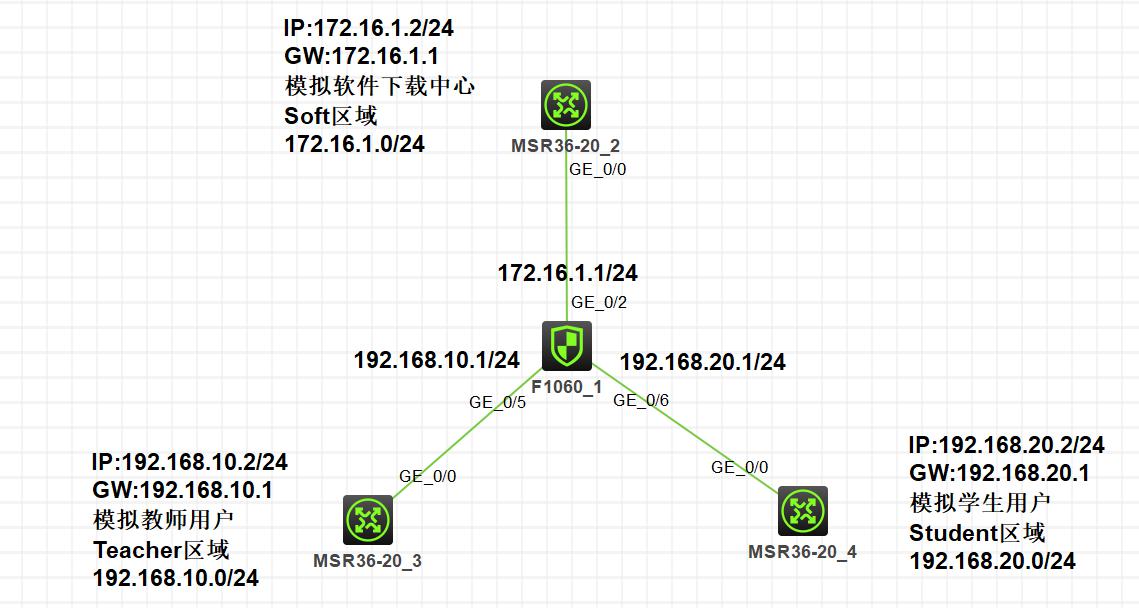
实验五:基于对象策略的区域访问配置
# 实验需求
1.通过配置对象策略,实现以下要求
- 允许教师用户区域在任意时间通过HTTP、ftp协议访问软件下载中心
- 允许学生用户区域在工作时间通过FTP访问软件下载中心,任何时间禁止通过HTTP访问软件下载中
# 实验解法
1.在防火墙上配置G1/0/2、G1/0/5、G1/0/6的接口IP地址,并在各安全域中添加相应接口
步骤一:ip地址配置略
步骤二:添加各安全域添加相应接口
[FW1]security-zone name soft
[FW1-security-zone-soft]import interface g1/0/2
[FW1]security-zone name Teacher
[FW1-security-zone-Teacher]import interface g1/0/5
[FW1]security-zone name Student
[FW1-security-zone-Student]import interface g1/0/6
2.配置IP地址对象组
步骤一:创建名为softadd的ip地址对象组,并定义其子网为172.16.1.0/24
[FW1]object-group ip address softadd
[FW1-obj-grp-ip-softadd]network subnet 172.16.1.0 24
步骤二:创建名为teacheradd的ip地址对象组,并定义其子网为192.168.10.0/24
[FW1]object-group ip address teacheradd
[FW1-obj-grp-ip-teacheradd]network subnet 192.168.10.0 24
步骤三:创建名为studentadd的ip地址对象组,并定义其子网为192.168.20.0/24
[FW1]object-group ip address studentadd
[FW1-obj-grp-ip-studentadd]network subnet 192.168.20.0 24
3.创建名为worktime的时间段,其时间范围为每周工作日的8点到18点
[FW1]time-range worktime 08:00 to 18:00 working-day
4.配置策略,可以采用以下 方法1 或者 方法2 其中的一种即可,如采用WEB配置方式即为方法1的方式
方式一:
步骤一:创建安全策略
[FW1]security-policy ip
步骤二:创建安全策略规则0,名称为teacher-soft
[FW1-security-policy-ip]rule 0 name teacher-soft
[FW1-security-policy-ip-0-teacher-soft]action pass
[FW1-security-policy-ip-0-teacher-soft]time-range worktime
[FW1-security-policy-ip-0-teacher-soft]source-zone teacher
[FW1-security-policy-ip-0-teacher-soft]destination-zone soft
[FW1-security-policy-ip-0-teacher-soft]source-ip teacheradd
[FW1-security-policy-ip-0-teacher-soft]destination-ip softadd
[FW1-security-policy-ip-0-teacher-soft]service ftp
[FW1-security-policy-ip-0-teacher-soft]service http
步骤三:创建安全策略规则1,名称为student-soft
[FW1-security-policy-ip]rule 1 name student-soft
[FW1-security-policy-ip-1-student-soft]action pass
[FW1-security-policy-ip-1-student-soft]source-zone student
[FW1-security-policy-ip-1-student-soft]destination-zone soft
[FW1-security-policy-ip-1-student-soft]source-ip studentadd
[FW1-security-policy-ip-1-student-soft]destination-ip softadd
[FW1-security-policy-ip-1-student-soft]service ftp
方式二:
步骤一:配置从teacher区域去往soft区域的对象策略,允许ftp和http,对象策略名称为teacher-soft
[FW1]object-policy ip teacher-soft
[FW1-object-policy-ip-teacher-soft]rule pass source-ip teacheradd destination-ip
softadd service ftp
[FW1-object-policy-ip-teacher-soft]rule pass source-ip teacheradd destination-ip
softadd service http
步骤二:配置从student区域去往soft区域的对象策略,工作时间允许ftp,任何时间丢弃http,对象策略名为student-soft
[FW1]object-policy ip student-soft
[FW1-object-policy-ip-student-soft]rule pass source-ip studentadd destination-ip
softadd service ftp time-range worktime
[FW1-object-policy-ip-student-soft]rule drop source-ip studentadd destination-ip
softadd service http
步骤三:在源安全域teacher和目的安全域soft之间,应用对象策略teacher-soft
[FW1]zone-pair security source teacher destination soft
[FW1-zone-pair-security-Teacher-soft]object-policy apply ip student-soft
步骤四:在安全域student和目的安全域soft之间,应用对象策略stduent-soft
[FW1]zone-pair security source student destination soft
[FW1-zone-pair-security-Student-soft]object-policy apply ip student-soft
5.结果检验
说明:因为这里soft服务器使用的是路由器模拟,所以这里只能区开启ftp服务演示效果,http我们可以替换成telnet进行测试,如果替换那么对象策略中的服务也要修改
步骤一:检验teacher访问soft可通过ftp、telnet(替换http后的服务)访问172.16.1.2,soft通过路由器模拟,开启telnet、ftp服务
<teacher>telnet 172.16.1.2
Trying 172.16.1.2 ...
Press CTRL+K to abort
Connected to 172.16.1.2 ...
******************************************************************************
* Copyright (c) 2004-2017 New H3C Technologies Co., Ltd. All rights reserved.*
* Without the owner's prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
******************************************************************************
login:
<teacher>ftp 172.16.1.2
Press CTRL+C to abort.
Connected to 172.16.1.2 (172.16.1.2).
220 FTP service ready.
User (172.16.1.2:(none)):
步骤二:在student上,检验是否可通过ftp访问服务器172.16.1.2,不能通过telnet访问172.16.1.2
<student>telnet 172.16.1.2
Trying 172.16.1.2 ...
Press CTRL+K to abort
Connected to 172.16.1.2 ...
Failed to connect to the remote host!
<student>
<student>ftp 172.16.1.2
Press CTRL+C to abort.
Connected to 172.16.1.2 (172.16.1.2).
220 FTP service ready.
User (172.16.1.2:(none)): zx
331 Password required for zx.
Password:
230 User logged in.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
6.为了更好的保证FTP传输安全,可以启用ASPF策略,ASPF(Advanced Stateful Packet Filter), 高级状态包过滤)的概念。ASPF能够实现主要功能由:应用层协议检测、传输层协议检测、ICMP差错报文检测、 TCP连接首包检测等。ASPF可以和包过滤防火墙ACL协同工作,也可以和对象策略object-policy协同工作, ACL或者object-policy负载按照规则进行报文过滤(阻断或放行)ASPF负载对以放行报文进行信息记录。
创建ASPF策略方式:
[FW1]aspf policy 1
[FW1-aspf-policy-1]detect ftp
[FW1]zone-pair security source teacher destination soft
[FW1-zone-pair-security-Teacher-Soft]aspf apply policy 1
[FW1-zone-pair-security-Teacher-Soft]qui
[FW1]zone-pair security source student destination soft
[FW1-zone-pair-security-Student-Soft]aspf apply policy 1